Three North Koreans have been indicted for allegedly taking part in a criminal conspiracy to steal or extort $1.3 billion in cryptocurrency and cash from banks and other organizations around the world, the U.S. Justice Department announced Wednesday.
In a 33-page federal indictment unsealed Wednesday, prosecutors allege that the hackers are part of an elite cyber unit – known as the Lazarus Group, APT38 or Hidden Cobra – within North Korea’s military intelligence operation, the Reconnaissance General Bureau.
“Simply put, the regime has become a criminal syndicate with a flag, which harnesses its state resources to steal hundreds of millions of dollars.”
— Assistant Attorney General John Demers
The indictment expands on a 2018 federal criminal complaint that outlined several cyber incidents and alleged criminal activity connected to this North Korean hacking group, including the creation of the malware used in the 2017 WannaCry global ransomware attack, the 2016 theft of $81 million from Bangladesh Bank and the 2014 attack on Sony Pictures Entertainment, according to the Justice Department.
Generating Funds for Government
Assistant Attorney General John Demers alleges that the hackers’ activities are part of an ongoing effort by the North Korean government to cope with international economic sanctions by funding the country’s regime through thefts from banks and other organizations in the U.S. and elsewhere (see: UN Report: N. Korea Targets Cryptocurrency Exchanges, Banks).
The indictment “also describes in stark detail how the Democratic People’s Republic of Korea cyber threat has followed the money and turned its revenue generation sights on the most cutting edge aspects of international finance, including through the theft of cryptocurrency from exchanges and other financial institutions, in some cases through the creation and deployment of cryptocurrency applications with hidden backdoors,” Demers says. “The indictment refines the attribution of this crime spree to the [North Korean] military intelligence services, specifically the Reconnaissance General Bureau. Simply put, the regime has become a criminal syndicate with a flag, which harnesses its state resources to steal hundreds of millions of dollars.”
John Hultquist, vice president of Mandiant Threat Intelligence, says: “It is no surprise that cybercrime has become a lifeline for North Korea, as they have steadily expanded criminal operations to include new complex heists, extortion and other ingenious schemes.”
The three alleged hackers charged in the indictment – Jon Chang Hyok, 31; Kim Il, 27; and Park Jin Hyok, 36 – are all members of the Reconnaissance General Bureau. Each is charged with one count of conspiracy to commit computer fraud and abuse, which carries a maximum sentence of five years in prison, and one count of conspiracy to commit wire fraud and bank fraud, which carries a maximum sentence of 30 years in federal prison, according to the Justice Department.
Because all three men are reportedly currently residing in North Korea, it’s unlikely they’ll ever face charges in the U.S. because North Korea does not extradite suspects to America.
Park has been previously charged for his alleged role in the Sony hack as well as other cybercriminal activity (see: Feds Charge North Korean With Devastating Cyberattacks).
Sprawling Hacking Activity
The new indictment outlines hacking activity allegedly carried out by the three suspects while they were stationed in Russia, China and elsewhere.
This includes attempts between 2015 and 2019 to steal more than $1.2 billion from banks in Vietnam, Bangladesh, Taiwan, Mexico, Malta and Africa by hacking networks and sending fraudulent messages through the banks’ SWIFT system accounts to transfer money to accounts they controlled.
The three were also allegedly involved in ATM “cash-out” schemes, including the theft of more than $6 million from BankIslami Pakistan Ltd. in October 2018.
The indictment also describes how the three alleged hackers, as well as others, targeted hundreds of cryptocurrency companies throughout the world to steal virtual currency. This includes $75 million stolen from a Slovenian cryptocurrency company in December 2017, $25 million from an Indonesian cryptocurrency company in September 2018, and almost $12 million from a financial services company in New York in August 2020. Prosecutors allege that during the attack against the New York firm last year, the hackers deployed a backdoor called the CryptoNeuro Trader.
Other alleged cybercriminal activity carried out by the three hackers includes ransomware and extortion attempts from 2017 through 2020 that involved stealing sensitive data and holding it for ransom and spear-phishing attacks that targeted the U.S. State and Defense departments, defense contractors and companies in the energy, aerospace and technology sectors.
In 2020, security firm McAfee described a North Korean-linked phishing campaign called “Operation North Star” that targeted U.S. aerospace and defense firm employees with fake job offer emails used to plant malware (see: North Korean Hackers Targeted US Aerospace, Defense Firms).
Malware Development
The unsealed indictment also provides details on how the North Korean hackers, along with others working for the regime, developed a family of malware called “AppleJeus” to target cryptocurrency exchanges to steal virtual currency.
Malware variants that are part of the AppleJeus family include Trojanized apps with legitimate-sounding names such as Celas Trade Pro, WorldBit-Bot, Union Crypto Trader, Kupay Wallet, CoinGo Trade, Dorusio, CryptoNeuro Trader and Ants2Whale, according to the Justice Department.
On Wednesday, the Cybersecurity and Infrastructure Security Agency, FBI and Treasury Department published a joint analysis of the malware and technical details of how the variants work.
The alert notes that many of these malware variants, which were portrayed as legitimate cryptocurrency trading apps, have been spotted in 30 countries since 2018. The operators used various means, such as social engineering tactics, phishing campaigns and ads on social media, to trick victims into downloading the malicious apps.
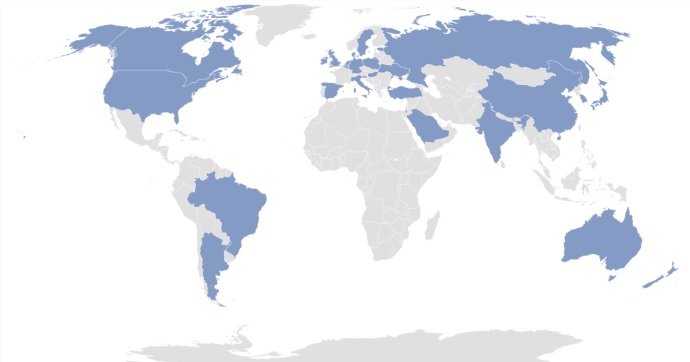 Countries where AppleJeus malware variants have been discovered (Source: CISA)
Countries where AppleJeus malware variants have been discovered (Source: CISA)
“In most instances, the malicious application – seen on both Windows and Mac operating systems – appears to be from a legitimate cryptocurrency trading company, thus fooling individuals into downloading it as a third-party application from a website that seems legitimate,” according to CISA.
Most of the malware acted as a backdoor to give the hackers access to networks or devices. From there, they could steal data or cryptocurrency, maintain persistence and plant other malicious code, according to the CISA alert.
Other security researchers have also published reports about these Trojanized currency trading apps (see: Phony Company Used to Plant macOS Malware: Report).
Another Arrest
Besides the unsealing of the indictment against the alleged North Korean hackers, the Justice Department also announced Wednesday that Ghaleb Alaumary, 37, of Ontario, Canada, who allegedly served as a high-level money launderer for criminal schemes, including ATM cash-out attacks conducted by the North Korean hacking group, has pleaded guilty to a money laundering charge.
Alaumary is also under investigation for his alleged involvement in a separate business email compromise scheme, the Justice Department notes. Plus, he’s alleged to have conspired with another man, Ramon Olorunwa Abbas of Nigeria, and others to launder funds from a North Korean cyber heist that targeted a Maltese bank in February 2019.
From: Bank Info Security