ESET: Some Attacks Happened Before Microsoft Was Notified of Vulnerabilities
At least 10 advanced persistent threat groups exploited unpatched Microsoft Exchange vulnerabilities in attacks against thousands of companies in the last three months, according to researchers at the Slovak security firm ESET.
ESET researchers posted details on each attack and either named the APT group involved or noted that an unknown gang conducted the hack. Several APT groups began their attacks before Microsoft was notified on Jan. 5 about the vulnerabilities, indicating they somehow gained knowledge of the flaws, ESET says.
“This suggests that multiple threat actors gained access to the details of the vulnerabilities before the release of the patch, which means we can discard the possibility that they built an exploit by reverse engineering Microsoft updates,” the report states.
Commenting on the report, Ben Read, director of analysis with Mandiant Threat Intelligence, says: “We can’t confirm the exact attribution that ESET is making, but the data we have does show multiple likely-China groups using the exploit in different waves, matching what ESET has seen.”
The APT Groups Involved
The APT groups ESET says it has identified as being involved in Exchange attacks are Tick, LuckyMouse, Calypso, Websiic, Winnti, Tonto Team, Mikroceen and DLTMiner. Two other groups involved have not yet been identified.
ESET had previously said that about five APT groups has been exploiting the four Exchange vulnerabilities – CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065, but it did not name those groups.
Earlier, Microsoft blamed the attacks on a single China-based group it calls Hafnium.
Drew Schmitt, a senior threat intelligence analyst at GuidePoint Security, points out: “As we have seen with the SolarWinds breach and now these Microsoft Exchange vulnerabilities, threat groups are targeting technology used by many to have the largest impact possible.”
The Targets
ESET found that the Exchange attacks have affected at least 5,000 government and private email servers in 115 countries.
The cybersecurity company Unit 221B, however, says it acquired a list of 86,000 IP addresses of Exchange servers infected worldwide, says Allison Nixon, the company’s chief research officer (see: List of Hacked Exchange Servers May Boost Recovery Efforts).
Unit 221B has created the web-based service Check My OWA, designed to help organizations identify whether their email systems were infected in the first wave of attacks, Nixon says.
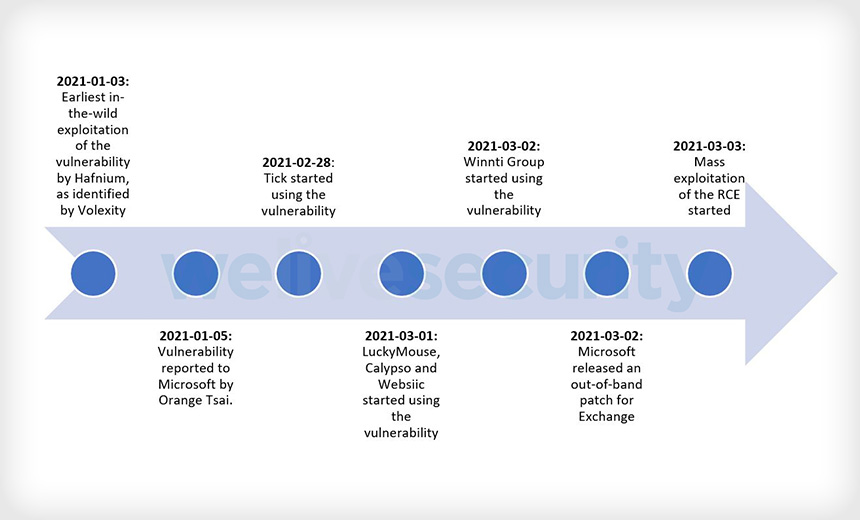
ESET says three of the 10 APT groups began exploiting the unpatched vulnerabilities in Exchange on Jan. 3, two days before Devcore security researcher Cheng-Da Tsai – also known as Orange Tsai – told Microsoft about the security flaws. One additional attack was observed on Feb. 28, two days before Microsoft issued an emergency patch. The six other APT groups began their activity after March 3, ESET reports.
The security company Volexity spotted hackers targeting Exchange servers on Jan. 3, when it saw CVE-2021-26855 being exploited. ESET is attributing this initial wave of attacks to the groups LuckyMouse, Calypso and Websiic.
LuckyMouse, also known as APT27, began its attack by dropping the Nbtscan tool, installing a variant of the ReGeorg web shell and issuing a GET request using curl. It then attempted to install the gang’s SysUpdate, according to ESET.
Calypso hit Mideast and South American targets using two web shells and two backdoors, ESET reports. It then installed a variety of Mimikatz malware, which is used as a post-exploitation tool to steal passwords from memory, as well as hashes, the researchers say.
Websiic’s activity involved targeting a cluster for seven email servers used by private companies in Asia and another server used by an Asian government, ESET found.
On Feb. 27, the APT group Tick, which has been operating since 2008, compromised the webserver of an East Asian IT company, the researchers say. After injecting a first-stage web shell that gave it the ability to issue orders to the device, the group dropped the Delphi backdoor.
Just hours before Microsoft issued its patch, Winnti, also known as Barium and APT41, hit an oil company and a construction equipment firm in East Asia, ESET says. This group used the PlugX RAT and ShadowPad malware.
Post-Patch Attacks
On March 4, the day after Microsoft issued its emergency patch, the other groups began their attacks. This activity included:
- Tonto Team, also known as CactusPete, hacked email servers of a procurement firm and a consulting company specializing in software development and cybersecurity, both based in Eastern Europe.
- An unknown group used the Opera browser to target about 650 servers, mostly in the U.S., Germany, the U.K. and other European countries, and then install the penetration testing tool Cobalt Strike.
- An unknown group installed web shells in four email servers in Asia and South America that, in turn, downloaded variants of the IIS backdoor, a rootkit for Microsoft Internet Information Services.
- The Mikroceen APT group, also known as Vicious Panda, on March 4 compromised the Exchange server of a utility company in Central Asia, injecting versions of Mimikatz.
- DLTMiner on March 5 deployed PowerShell downloaders on email servers that were previously targeted using Exchange vulnerability exploits. ESET theorizes that DLTMiner is hijacking web shells installed by other threat groups.
Help for Defenders
Knowing the specific groups that are attacking vulnerable Exchange servers is a huge plus for defenders, says GuidePoint Security’s Schmitt.
“As defenders begin to have a more detailed grasp on threat groups and their methodology, they can implement defense-in-depth strategies that will provide the most layers of protection in their environments.”
From: bankinfosecurity