Lazarus, the North Korean-backed advanced persistent threat group, has been conducting a campaign striking defense industry targets in more than a dozen countries using a backdoor called ThreatNeedle that moves laterally through networks and can overcome network segmentation, according to researchers at Kaspersky.
This ongoing campaign, which started in 2020, uses a multistep approach that begins with a relatively basic but well-thought-out spear-phishing attack leading eventually to Lazarus gaining full control over the victim’s device, the researchers note.
ThreatNeedle, which is part of Lazarus’ Manuscrypt family of malware, also can access and steal data from segmented portions of a network not directly connected to the internet, Kaspersky says.
“We observed how they overcame network segmentation by gaining access to an internal router machine and configuring it as a proxy server, allowing them to exfiltrate stolen data from the intranet network to their remote server,” say Seongsu Park and Vyacheslav Kopeytsev, senior threat researchers with Kaspersky.
This not the first time ThreatNeedle has been used by Lazarus, also known as APT38 and Hidden Cobra. Starting in February 2018, the North Korean hacking group began leveraging it against a cryptocurrency exchange in Hong Kong and an unnamed mobile game developer, the researchers note.
Earlier this month, three North Koreans associated with Lazarus were indicted by the U.S. Justice Department for allegedly taking part in a criminal conspiracy that attempted to steal or extort $1.3 billion in cryptocurrency and cash from banks and other organizations around the world. It is not known if these three were involved in the attack cited by Kaspersky.
Once downloaded and functioning, the malware can manipulate files and directories, conduct system profiling, control backdoor processes, force the device to enter sleep or hibernation mode, update the backdoor configuration and execute received commands, according to the report.
Overcoming Network Segmentation
The most dangerous aspect of the campaign for defense contractors and other potential targets that operate an industrial plant is Lazarus’ ability to overcome network segmentation defenses and move laterally into networks isolated from the internet, the Kaspersky researchers note.
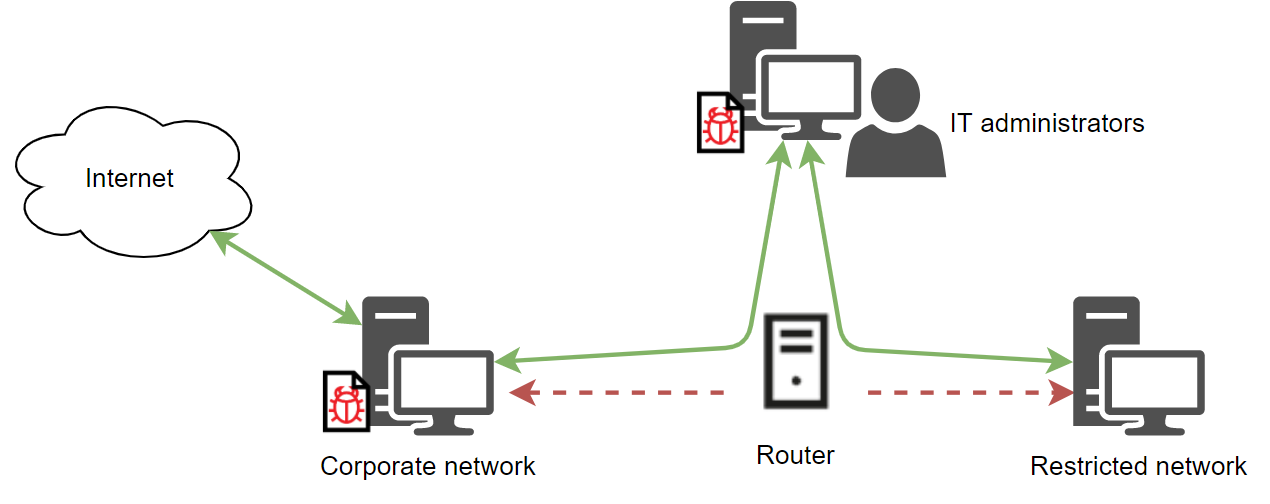 The connection layout between a victim’s network segments and how it is overcome
The connection layout between a victim’s network segments and how it is overcome
Kaspersky analyzed one victim that divided its network into a corporate segment on which computers had internet access and a restricted portion of the network that hosted sensitive data, but had no direct internet access. The company believed it had set up the network so no data could be shared between the two segments.
But this was not completely true. IT administrators on the corporate segment could connect to the restricted area to conduct maintenance, which the attacker discovered after thoroughly infecting the corporate network, including the IT department’s computers, with malware.
The attackers then used the IT department’s computers to connect with the segmented portion of the network, which entailed finding the router used to connect to the isolated segment. In one case investigated, the attackers accomplished this by finding the router’s credentials stored inside the system.
“The attackers scanned the router’s ports and detected a Webmin interface. Next, the attackers logged in to the web interface using a privileged root account,” the researchers say.
This effectively turned the company’s server into a proxy, enabling malware to be downloaded into the segmented portion of the network and remove data.
Initiating the Attack
As with other Lazarus campaigns, the initial entry point is made through a spear-phishing campaign, albeit, in this case, one developed with a great deal of care and deployed by a very persistent team, the researchers say.
The phishing email itself is basic, containing a malicious Microsoft Word document or a link to a malicious remote server. The social engineering in these attacks uses topics of interest to the target. Additionally, the attacker writes the content as if it is coming from the organization under attack, the report notes.
The email recipient is chosen using publicly available information, which is then used in the email to make it more convincing. The malware is injected if the malicious document or website is accessed, the researchers say.
One point Kaspersky specifically called out is that the attacker would not despair if an attack was initially unsuccessful. Instead, they would follow up with additional emails containing slightly different information or tips on enabling Word macros to try and convince the person to take action.
ThreatNeedle
Once the victim clicks the document or link, the first stage of the ThreatNeedle backdoor malware is dropped, enabling the attacker to gain control of the target system, according to Kaspersky. The attacker uses this access to conduct an initial recon and then deploy additional malware that will allow it to move laterally through the system.
The backdoor itself is encrypted and embedded in the malware code requiring an RC4, or Rivest Cipher 4, key to decrypt. The dropped malware is registered as a Windows service and launched. In addition, the malware saves the configuration data as a registry key encrypted in RC4, the researchers say.
The data exfiltration phase then begins with, in one case, the attacker used a custom tunneling tool to create covert Secure Shell – SSH – tunnels to a remote server located in South Korea. Lazarus uses a simple binary encryption in this process. The tool is quite basic with the ability to forward traffic to the server, the researchers say.
From: Bank Info Security