The U.S. Justice Department and Bulgarian authorities have seized servers and disrupted the infrastructure and darknet websites of the NetWalker ransomware gang. They’ve also made one arrest.
The news comes the same week that Europol announced that a multinational law enforcement operation disrupted the notorious Emotet botnet’s infrastructure by gaining control of hundreds of servers. That botnet was used to distribute ransomware and other malware.
Police Action
In the Netwalker takedown, police have confiscated hundreds of thousands of dollars in ransom payments collected by the cybercriminal gang, federal prosecutors note.
NetWalker, a ransomware-as-a-service cybercriminal operation, has been active since 2019. It uses an affiliate model, in which the operators maintain and update the crypto-locking malware while others perform such tasks as gaining initial entry into victims’ networks, in exchange for a share of the profits.
The ransomware has been tied to a number of high-profile attacks in 2020, including one that targeted the University of California San Francisco, which paid a ransom of more than $1 million (see: FBI: COVID-19-Themed Phishing Spreads Netwalker Ransomware).
And in February 2020, Australian transportation and logistics company Toll Group was hit by the ransomware group.
Arrest Made
On Wednesday, the Justice Department announced the indictment of Sebastien Vachon-Desjardins, a Canadian national who is suspected of working as a NetWalker affiliate and helping to conduct a ransomware attack against a victim in Florida. Vachon-Desjardins is alleged to have made $27.6 million from infecting victims with the NetWalker ransomware.
Vachon-Desjardins has been charged with intentional damage to a protected computer, which carries a maximum sentence of 10 years in federal prison, the federal indictment notes.
Bulgarian authorities have seized the servers used to support the darknet sites used by NetWalker ransomware affiliates to provide payment instructions and communicate with victims, according to the Justice Department.
The federal indictment also notes that on Jan.10, the FBI seized cryptocurrency worth more than $450,000 that NetWalker-affiliated gangs received in ransom payments.
“Ransomware groups have had operation with near complete impunity for far too long, so this is great to see,” says Brett Callow, a threat analyst at security firm Emsisoft. “We need strong action to combat the ransomware epidemic, and this is certainly a step in the right direction.”
Suspect’s Role
Blockchain analysis firm Chainalysis, which assisted the law enforcement agencies in identifying the cryptocurrency wallets tied to NetWalker, notes Vachon-Desjardins was allegedly responsible for accessing victims’ networks by deploying the malware. Chainalysis has identified 345 addresses allegedly associated with Vachon-Desjardins dating to 2018, with some of the addresses receiving transactions as recently as Wednesday.
The Chainalysis report also notes that Vachon-Desjardins was allegedly involved in at least 91 NetWalker attacks since April 2020 and received 80% of the ransom for his role in deploying the ransomware.
“[Vachon-Desjardins] allegedly received more than $14 million worth of bitcoin at the time of receipt of the funds, ultimately possessing at least $27.6 million given its rising value,” the Chainalysis report notes.
Vachon-Desjardins is also suspected of working as an affiliate for a number of other ransomware-as-a-service operations, including Sodinokibi, Suncrypt and Ragnar Locker, according to the Chainalysis report.
NetWalker’s Profits
The Chainalysis report notes that NetWalker is estimated to have earned approximately $46 million in ransom payments since these attacks began. The group’s fewer than 20 affiliate groups earned between 76% and 80% of the ransom profits, the company’s report notes.
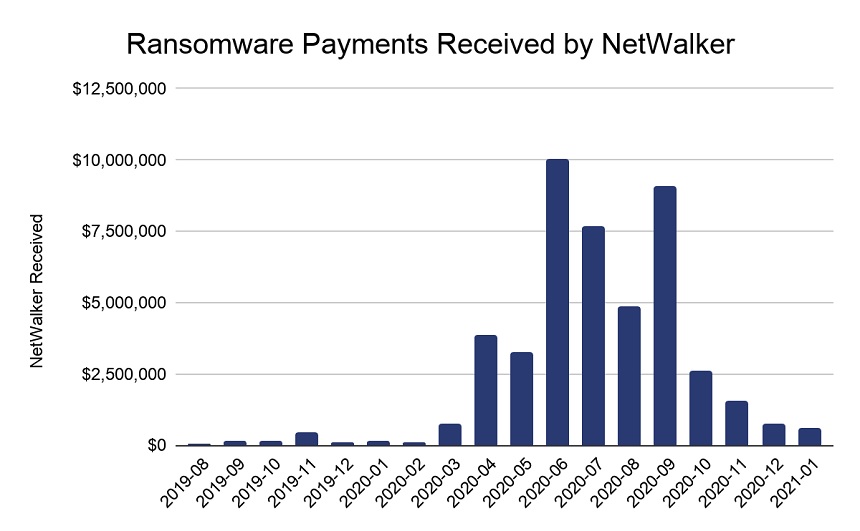 (Source: Chainalysis)
(Source: Chainalysis)
The report also says NetWalker was most active in mid-2020, when the average ransom per incident grew to $65,000 from $18,800 in 2019.
The FBI said in a July 2020 alert that two of the most common vulnerabilities exploited by Netwalker over the last year are CVE-2019-11510, which is found in Pulse Secure VPN servers, and CVE-2019-18935, which is found in Telerik UI, a toolset used with Windows Presentation Foundation to help build applications.
The FBI alert also noted that last year, the operators behind Netwalker were luring victims with pandemic-themed phishing emails that contained an attachment with a malicious VBS, or Visual Basic Scripting, script that executed the payload once opened.
Source: bankinfosecurity