Regulation Requires Russians to Disclose Their Cryptocurrency Transactions – Or Else
Did Russia pass a tough new cryptocurrency law to help authorities recruit or compel criminal hackers to assist the government?
That’s the thesis of a new report from New York-based threat intelligence firm Advanced Intelligence, aka AdvIntel. While a new law in Russia that took effect on Jan. 1 provides a legal framework for using cryptocurrency, it also includes a host of provisions designed to unmask users of bitcoins, monero and other virtual currencies, the report notes.
“By enforcing the cryptocurrency law, the Russian government builds the legal base for overtaking the power and establishing total control over the dark web market, including the ransomware sector.”
“The new Russian crypto law requires all cryptocurrency holders, including individuals, companies and Russian authorities, to report their crypto transactions and wallet balances if the transaction amounts exceed 600,000 rubles – approximately $8,124 – in a calendar year,” Anastasia Sentsova, an analyst at AdvIntel, and Yelisey Boguslavskiy, the firm’s CEO, write in the report. “Failing to report twice in three years or providing inaccurate information will result in monetary fines, forced labor and imprisonment.”
Ostensibly, the law is designed “to prevent illegal cryptocurrency transactions and money laundering,” the AdvIntel researchers say. But in reality, the move might be an attempt “to monopolize the dark web market, including the ransomware sector, by excluding competitors who interfere with government plans and take away the profit,” they say. It also could be part of an attempt to “recruit new hackers” to assist government offensive hacking teams.
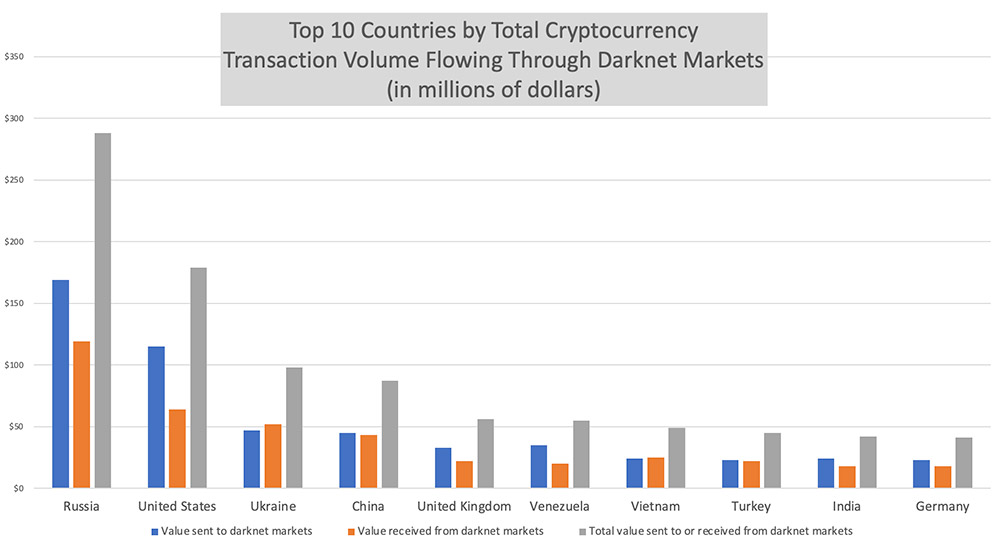
Russia’s Cryptocurrency Regulation
Russian President Vladimir Putin last August signed into law the bill, which legalizes cryptocurrency, albeit with a host of caveats.
As noted, the law took effect on Jan. 1, and Russian news agency TASS says the law states that “digital currency cannot be used … to pay for any goods and services,” although it can be bought, sold, exchanged or pledged, Bitcoin.com reports.
Under the law, banks and exchanges in Russia can handle digital currency, provided they register with the Bank of Russia – the country’s central bank – and maintain a register of all operators and transactions. The law also states that only institutions and individuals who have declared transactions to authorities can later seek redress in court, for example, if someone steals their cryptocurrency.
“In Russia, the use of bitcoin and other crypto assets as a means of payment is prohibited. There are no signs that a change in legislation allowing crypto assets to be used as a means of payment in Russia will be forthcoming,” legislator Anatoly Aksakov, the chief backer of legislation designed to regulate the use of cryptocurrency, told Russian radio station Govorit Moskva last month.
“Taxation, compulsory declaration – these things are already enforced by law,” said Aksakov, who chairs the State Duma – the lower house of the country’s parliament – Committee on the Financial Market. And going forward, he predicted “there will only be more and more control over the holding of cryptocurrencies.”
Cybercrime Rules for Russians
Security experts say that for years, Russian officials and intelligence agencies have looked the other way when it comes to cybercrime, so long as criminals follow this rule: Never hack Russians or allied countries.
That’s one reason why many types of malware will check an infected system’s language and not execute if it’s set to Russian. Many ransomware gangs also studiously avoid targeting any individual or organization in the Commonwealth of Independent States, or CIS, which is composed of many of the nations that formerly comprised the Soviet Union: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan and Uzbekistan.
Cybercrime continues to flourish, in part, because many criminals are working from Russia, which never extradites citizens, thus making their activities difficult for Western law enforcement agencies to disrupt. Russian-language darknet markets – led by Hydra – and cybercrime forums also continue to flourish, providing a ready supply of hacking tools, expertise, stolen payment card details, money laundering services, connections and other cornerstones of today’s cybercrime-as-a-service ecosystem.
‘Do Us a Favor’
Another cybercrime truism in Russia is that in exchange for authorities looking the other way, the government may sometimes ask criminals for a favor.
And some intelligence agency hackers – including in Russia – appear to hack for profit in their free time.

Conversely, intelligence agencies – in Russia and other countries – may have moles inside cybercrime gangs. Using ransomware, for example, would be the perfect cover for an intelligence operation.
Historically, nation-state attackers have sometimes employed tools or infrastructure associated with a different country’s government-run offensive hacking teams to run false flag operations that point the finger at another country. And sometimes, they’ve used criminal toolsets, tactics and infrastructure to make hack attacks not appear to have been espionage-focused.
In 2017, The New York Times reported that Evgeniy M. Bogachev, the alleged hacker and Gameover Zeus botnet mastermind who has a $3 million FBI bounty on his head, might have been helping Russian spies. Circumstantial evidence suggested Bogachev had allowed Russian intelligence agencies to piggyback on Gameover Zeus banking Trojan infections and raid infected PCs for intelligence.
Crypto-Locking Malware: Massive Profits
Ransomware remains today’s biggest cybercrime success story. Since Maze in late 2019 pioneered the “ransomhacking” trend of exfiltrating data before crypto-locking systems, to better pressure victims into paying a cryptocurrency ransom, gangs now often also hold potentially sensitive or confidential information on numerous organizations.
Obviously, this information might be of great interest to intelligence agencies. Accordingly, might some ransomware gangs have a Russian government nexus?
But with so many criminals who operate online apparently tracing to Russia – including ransomware developers, the operators of gangs, and affiliates who participate in ransomware-as-a-service operations – it’s a no-brainer that at least some of them have been co-opted by authorities or work for them.
An Attempt to Control Dark Web Market?
Many ransomware gangs claim to be apolitical and purely profit-focused, AdvIntel notes. But Russia’s new cryptocurrency-regulating law could change the calculus by threatening gangs’ profits unless they report any sum total of proceeds greater than $8,124 per year.
Any Russian gang that fails to do so “is essentially challenging the Russian state,” the AdvIntel researchers say in their report.
Voila: “The ransom business suddenly becomes political, whether the syndicates want it to be or not – and this adds an entire new layer for the cryptolocker pandemic which, until these days, was explicitly about money,” they say. “By enforcing the cryptocurrency law, the Russian government builds the legal base for overtaking the power and establishing total control over the dark web market, including the ransomware sector.”
While that might sound far-fetched, Russia has a massive – if illicit – domestic profit-making sector in the form of cybercrime and associated services. Given that the nation historically has allowed such enterprises to flourish, provided they occasionally work for the state and only target foreigners, would it be any surprise that the government might try to bring cryptocurrency-generating businesses, and potentially also some of those profits, under its wing?
More on crypto exchange security here.
From: Bank Info Security